約1か月ぶりのアップデートになります。
更新内容
更新内容は以下の通り。
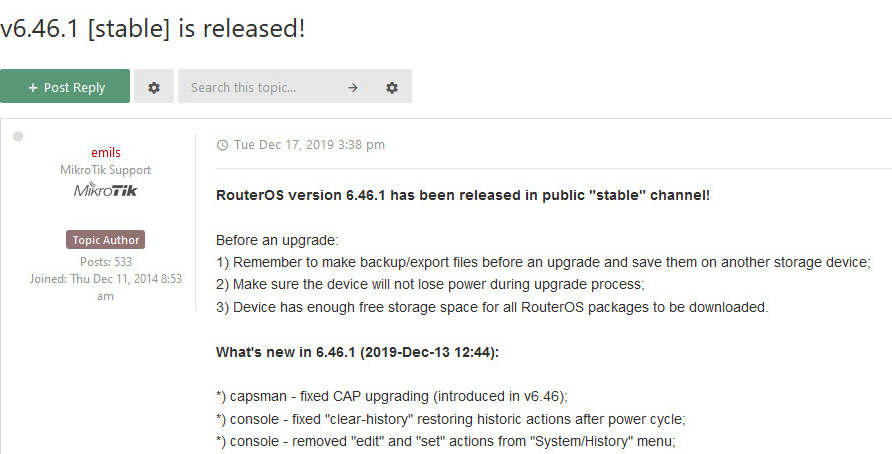
What's new in 6.46.2 (2020-Jan-14 07:17): *) chr - improved stability when changing ARP modes on e1000 type adapters; *) console - prevent "flash" directory from being removed (introduced in v6.46); *) console - updated copyright notice; *) crs305 - disable optical SFP/SFP+ module Tx power after disabling SFP+ interface; *) defconf - fixed "caps-mode" not initialized properly after resetting; *) defconf - fixed default configuration loading on RBwAPG-60adkit (introduced in v6.46); *) lora - fixed packet sending when using "antenna-gain" higher than 5dB; *) lte - fixed "cell-monitor" on R11e-LTE in 3G mode; *) lte - fixed "earfcn" reporting on R11e-LTE6 in UMTS and GSM modes; *) lte - report only valid info parameters on R11e-LTE6; *) ppp - fixed minor typo in "ppp-client" monitor; *) qsfp - do not report bogus monitoring readouts on modules without DDMI support; *) qsfp - improved module monitoring readouts for DAC and break-out cables; *) routerboard - added "mode-button" support for RBcAP2nD; *) security - fixed vulnerability for routers with default password (limited to Wireless Wire), admin could login on startup with empty password before default configuration script was fully loaded; *) system - fixed "*.auto.rsc" file execution (introduced in v6.46); *) system - fixed "check-installation" on PowerPC devices (introduced in v6.46); *) traffic-generator - improved memory handling on CHR; *) webfig - allow skin designing without "ftp" and "sensitive" policies; *) webfig - fixed "skins" saving to "flash" directory if it exists (introduced in v6.46); *) winbox - automatically refresh "Packets" table when new packets are captured by "Tools/Packet Sniffer"; *) winbox - fixed "Default Route Distance" default value when creating new LTE APN; *) winbox - removed duplicate "join-eui" and "dev-eui" parameters under "Lora/Traffic";
まず最初にセキュリティに関して “fixed vulnerability for routers with default password (limited to Wireless Wire), admin could login on startup with empty password before default configuration script was fully loaded;“という記述が見られますが、最近以下に報告された脆弱性に関しての修正なのか不明です。

Full Disclosure: Two vulnerabilities found in MikroTik's RouterOS
別件ですが
Mikrotikの脆弱性を悪用されCryptjackingに大量に使用されていた問題について、インターポール( 国際刑事警察機構)はGoldfish Alphaと呼ばれる作戦が実行され、 地域全体での感染したデバイス数の大幅な減少に成功したようです。
[Interpol] Operation Goldfish Alpha - MikroTik

Operation Goldfish Alpha reduces cryptojacking across Southeast Asia by 78%
Interpol and CERT teams from 10 Southeast Asian countries crack down on hacked MikroTik routers.
ダウンロード

MikroTik
MikroTik makes networking hardware and software, which is used in nearly all countries of the world. Our mission is to make existing Internet technolo...
フォーラム
v6.46.2 [stable] is released! - MikroTik